shivajikobardan
- 637
- 54
- Homework Statement
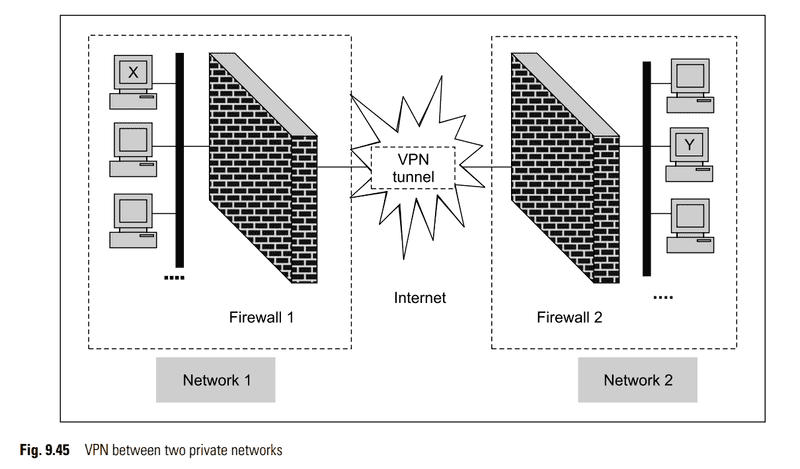
- VPN-Virtual Private Network
- Relevant Equations
- None
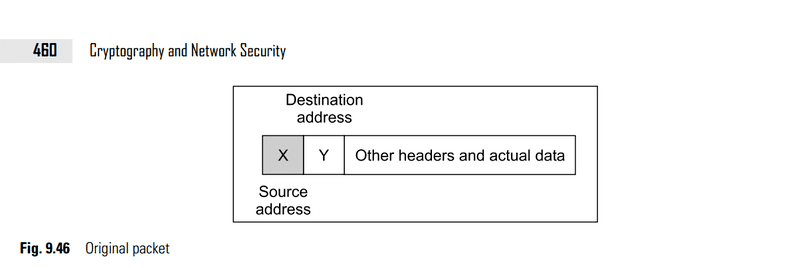
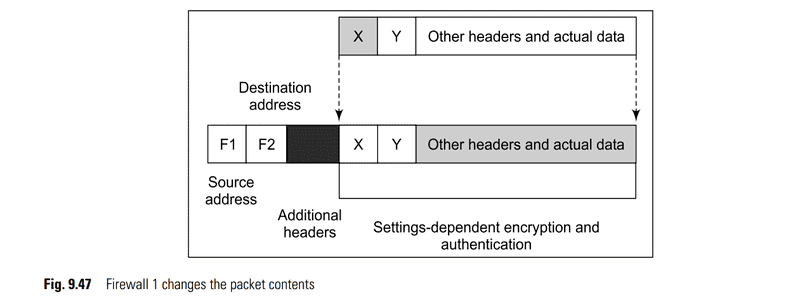
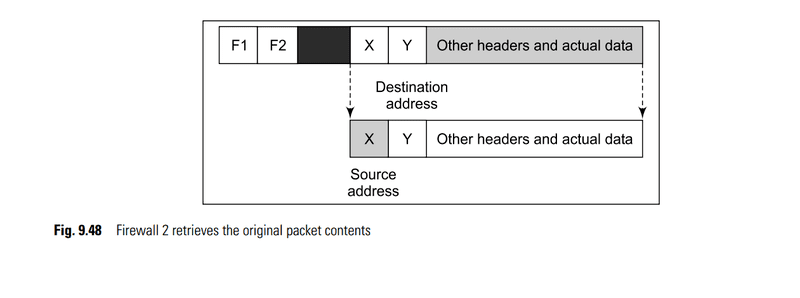
What’s encrypted here? Is the source and destination IP address encrypted? Is the firewall1 address and firewall2 address encrypted? Is the payload also encrypted?
Is this all what a VPN does? I can’t really believe that VPN only encapsulates and encrypts.
If it’s encrypting the source and destination IP address, is encapsulating with firewall address necessary? Because nobody is going to find about that.
I feel I'm missing some crucial information about the intricacy of VPN working. So, please guide.
Is this all what a VPN does? I can’t really believe that VPN only encapsulates and encrypts.
If it’s encrypting the source and destination IP address, is encapsulating with firewall address necessary? Because nobody is going to find about that.
I feel I'm missing some crucial information about the intricacy of VPN working. So, please guide.