- 2,180
- 2,691
I was trying to paste the hosts file in this thread, and ran into an exception:
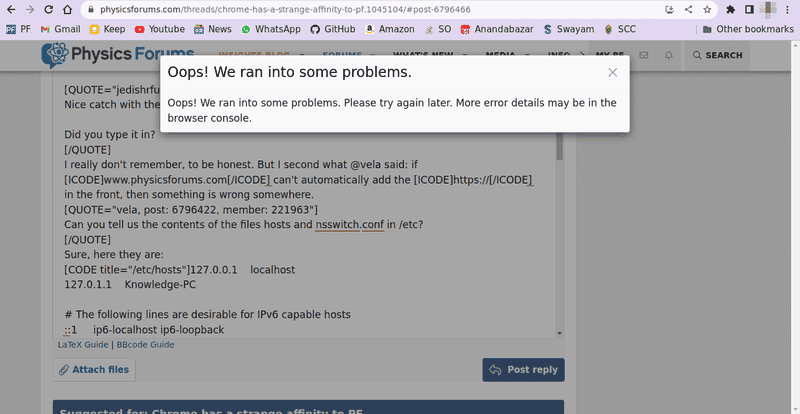
I can't paste the full error message from the console because PF is not allowing me to do so. Here is the error message:
Upon further testing, it turns out that I can paste the hosts file, but cannot type
I can't paste the full error message from the console because PF is not allowing me to do so. Here is the error message:
Sorry, you have been blocked
You are unable to access physicsforums.com
Why have I been blocked?
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
What can I do to resolve this?
You can email the site owner to let them know you were blocked. Please include what you were doing when this page came up and the Cloudflare Ray ID found at the bottom of this page.
Cloudflare Ray ID: 743cfbb7cc8df8d7 • Your IP: <Removed_by_me> • Performance & security by Cloudflare
Upon further testing, it turns out that I can paste the hosts file, but cannot type
/ etc / hosts (without the spaces). Neither in code blocks nor as plain text.