PainterGuy
- 938
- 73
Hi,
I had thought that "hill climbing method" is a general terminology to refer to methods such as perturb and observe and incremental conductance. The same is also said here, "The hill climbing based techniques are so named because of the shape of the power-voltage (P-V) curve. This technique is sub-categorized in three types: Perturb & Observe Algorithm (P&O), Modified Adaptive P & O Method, Incremental Conductance Algorithm (INC)". [Reference #1, page #91: https://www.academia.edu/5691750/Hi..._point_in_Solar_Photovoltaic_Systems-A_Review]
But at many places they are considered two different methods, for example, "Perturbation and observation (P&O) and hill climbing methods are widely applied in the MPPT controllers due to their simplicity and easy implementation [2-3]. P&O method involves a perturbation in the operating voltage of the PV array, while hill climbing strategy introduces a perturbation in the duty ratio of the power converter [2] and is more attractive duty to the simplified control structure [4][Reference #2, page #804: https://www.researchgate.net/publication/224321861_Comparison_of_PO_and_hill_climbing_MPPT_methods_for_grid-connected_PV_converter]
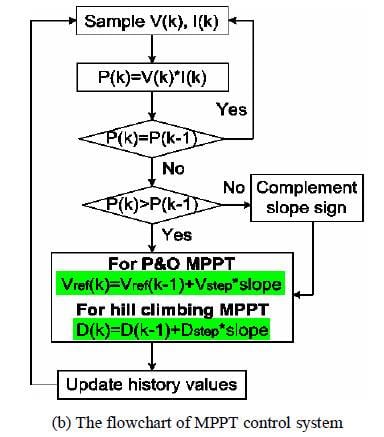
Reference #2, page #805, also lists a flow diagram. Near the end it makes a distinction between perturb and observe algorithm and hill climbing by saying "For P&O MPPT Vref(k)=Vref(k+1)+Vstep*slope" and "For hill climbing MPPT D(k)=Dref(k-1)+Dstep*slope". I understand the hill climbing and how duty cycle is used to change the input voltage of panel to operate it at maximum power point. P&O changes the Vref instead of duty cycle but it can only change the Vref through duty cycle. For both methods, at the end od day, it's the duty cycle which regulates the voltage. So, does the difference only lie in the wording, or is there more to it? Could you please help me with this? Thank you.
Reference #11: https://drive.google.com/open?id=1JQ4wQkA-M9PwBmRS6xHLhTBLZv3Dk7ou
Reference #2: https://drive.google.com/open?id=1qthgR8rW572jaaAjmvDFRvnkqtd10mZk
I had thought that "hill climbing method" is a general terminology to refer to methods such as perturb and observe and incremental conductance. The same is also said here, "The hill climbing based techniques are so named because of the shape of the power-voltage (P-V) curve. This technique is sub-categorized in three types: Perturb & Observe Algorithm (P&O), Modified Adaptive P & O Method, Incremental Conductance Algorithm (INC)". [Reference #1, page #91: https://www.academia.edu/5691750/Hi..._point_in_Solar_Photovoltaic_Systems-A_Review]
But at many places they are considered two different methods, for example, "Perturbation and observation (P&O) and hill climbing methods are widely applied in the MPPT controllers due to their simplicity and easy implementation [2-3]. P&O method involves a perturbation in the operating voltage of the PV array, while hill climbing strategy introduces a perturbation in the duty ratio of the power converter [2] and is more attractive duty to the simplified control structure [4][Reference #2, page #804: https://www.researchgate.net/publication/224321861_Comparison_of_PO_and_hill_climbing_MPPT_methods_for_grid-connected_PV_converter]
Reference #2, page #805, also lists a flow diagram. Near the end it makes a distinction between perturb and observe algorithm and hill climbing by saying "For P&O MPPT Vref(k)=Vref(k+1)+Vstep*slope" and "For hill climbing MPPT D(k)=Dref(k-1)+Dstep*slope". I understand the hill climbing and how duty cycle is used to change the input voltage of panel to operate it at maximum power point. P&O changes the Vref instead of duty cycle but it can only change the Vref through duty cycle. For both methods, at the end od day, it's the duty cycle which regulates the voltage. So, does the difference only lie in the wording, or is there more to it? Could you please help me with this? Thank you.
Reference #11: https://drive.google.com/open?id=1JQ4wQkA-M9PwBmRS6xHLhTBLZv3Dk7ou
Reference #2: https://drive.google.com/open?id=1qthgR8rW572jaaAjmvDFRvnkqtd10mZk