evinda
Gold Member
MHB
- 3,741
- 0
Hello! (Smile)
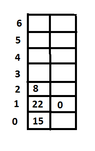
There are given three elements with keys $22, 15, 8$. Insert them in the given order in a hashtable of $7$ positions given that as method of treatement of the collisions we use:
That's what I have tried:
For the first case:
View attachment 3894
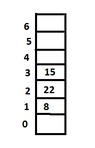
For the second case:
View attachment 3895Could you tell me if it is right? (Thinking)
There are given three elements with keys $22, 15, 8$. Insert them in the given order in a hashtable of $7$ positions given that as method of treatement of the collisions we use:
- hashing that follows the method coalesced chaining with the hash fuction $h(k)=k \mod m$
- ordered hashing with open addressing strategies with the primary hash function $h_1(x)=x \mod m$ and the secondary hash function $h_2(x)=(x^2+1) \mod{7}$
That's what I have tried:
For the first case:
View attachment 3894
For the second case:
View attachment 3895Could you tell me if it is right? (Thinking)